The DV Fraud Lab is renowned for uncovering sophisticated and complex fraud schemes like CycloneBot and SmokeScreen, all of which require advanced detection methods. However, every so often, a basic fraud scheme will surface and still manage to produce millions of daily impressions on unprotected campaigns. These simpler schemes, often marked by glaring mistakes and easily detectable patterns, serve as a reminder that not all fraudsters possess the same level of expertise. The DV Fraud Lab’s robust technology and vigilant monitoring strive to ensure that even the most rudimentary attempts at ad fraud are swiftly identified and addressed, maintaining the integrity of the digital advertising ecosystem.
One recent example is ShadowBot — a bot operation targeting mobile and Connected TV (CTV) ad environments, first uncovered by the DV Fraud Lab in 2024. This bot generates falsified ad impressions by using emulators and other automation methods to mimic mobile devices and spoof app IDs.
Some facts about ShadowBot include:
-
ShadowBot spoofed over 35 million unique mobile devices in Q1 2025.
-
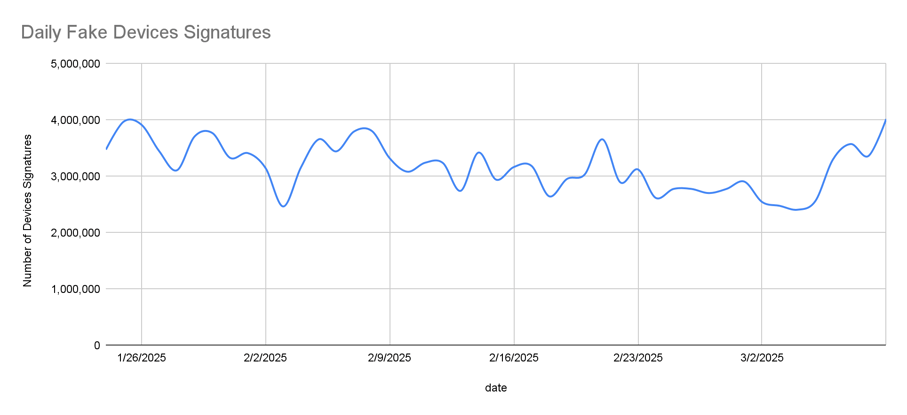
Over 3 million device signatures are generated each day by ShadowBot.
-
DV estimates that Shadowbot cost unprotected advertisers up to $2.5 million since the beginning of 2025.
The scheme leverages mobile emulators combined with VPN IPs to impersonate real users. Yet, their impersonation was rudimentary. The fraudsters made five mistakes, which we’ve outlined below.
Top 5 Fraudster Mistakes that Led DV to ShadowBot
1. Basic Automation Methods
The use of emulators can sometimes result in basic screen sizes that are common in automated traffic. For example, 800×600 is screen resolution that is associated with old square monitors and is a common default for non-human activity like virtual machines and automated scrapers.
ShadowBot devices tried to impersonate mobile devices, which have much smaller screen sizes with different proportions.
2. Overly Aggressive Traffic Generation
Fraudsters tend to get greedy and produce high volumes of fake traffic that are inconsistent with seasonal trends, as shown in the plot below:
3. Obscure Anonymizing IP Proxies
The fraudsters leveraged non-transparent anonymizing IP proxies. A quick look into one of them, as attached in the screenshot below, reveals obvious oversights. Client testimonials attributed to generic names like “John Doe” and “Jane Smith,” fake images and broken URLs are all indications of non-transparent behavior. In addition, some of its IPs have been reported for abuse by third-party IP reporting sites.
As is further illustrated below, the fraudster also failed to simulate realistic IP activity.
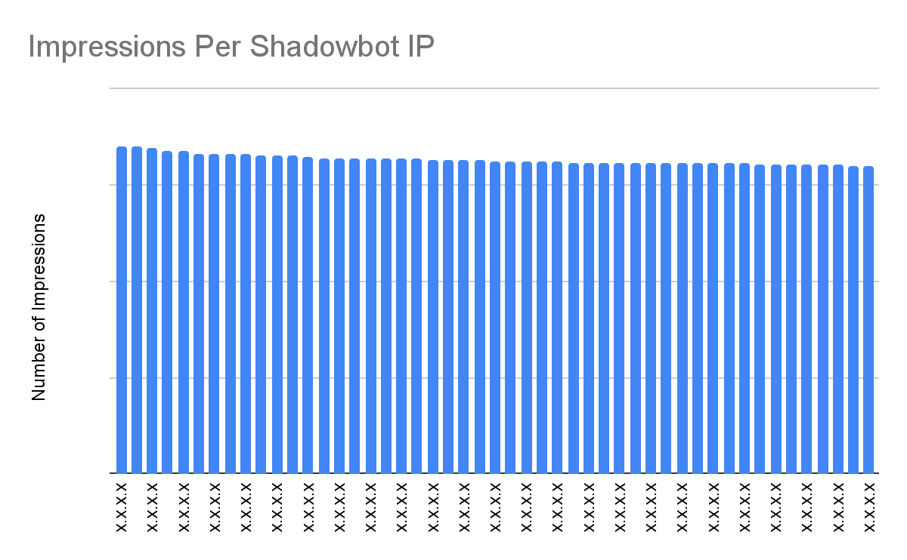
4. Lack of Diversification in User Behavior
The fraudster’s oversight in ignoring device diversity was another clue. Each device had almost exactly the same number of impressions, which is highly suspicious.
5. Improbable User Activities
DV’s analytics tools are adept at identifying patterns that deviate from normal user behavior, and in ShadowBot’s case, each device visited a large number of falsified bundles in a very short period of time. Per ShadowBot’s device behavior, illustrated below, the devices “switched” through 10 applications in a mere 9 minutes — this is a pattern that makes no sense for a genuine human user (most of us may play 1 or 2 mobile games daily, but not 10 games in 9 minutes). As mentioned above, the applications are spoofed and aren’t involved in IVT activities.
DV Has Got You Covered
DV has identified dozens of web, in-app and streaming/CTV fraud schemes over the past few years. Certain types of fraud are more challenging to detect, as they often involve legitimate devices and apps that are not harmful on their own. DV has developed sophisticated tools and algorithms to accurately identify the individual impressions that are infected and provide maximum protection to clients. DV remains committed to providing advertisers with the tools and insights needed to manage ad fraud effectively, taking steps to ensure that every client’s campaign delivers accurate, trustworthy results.





